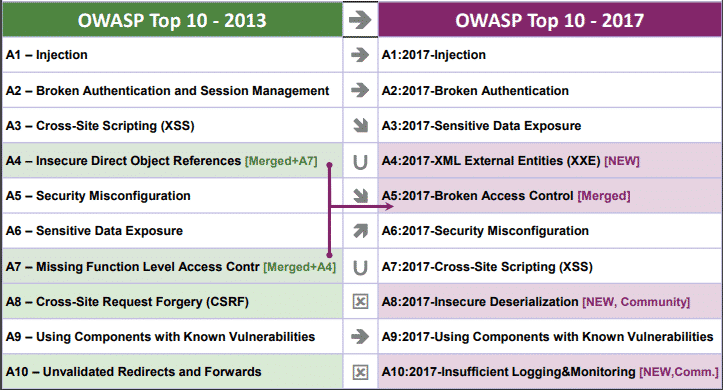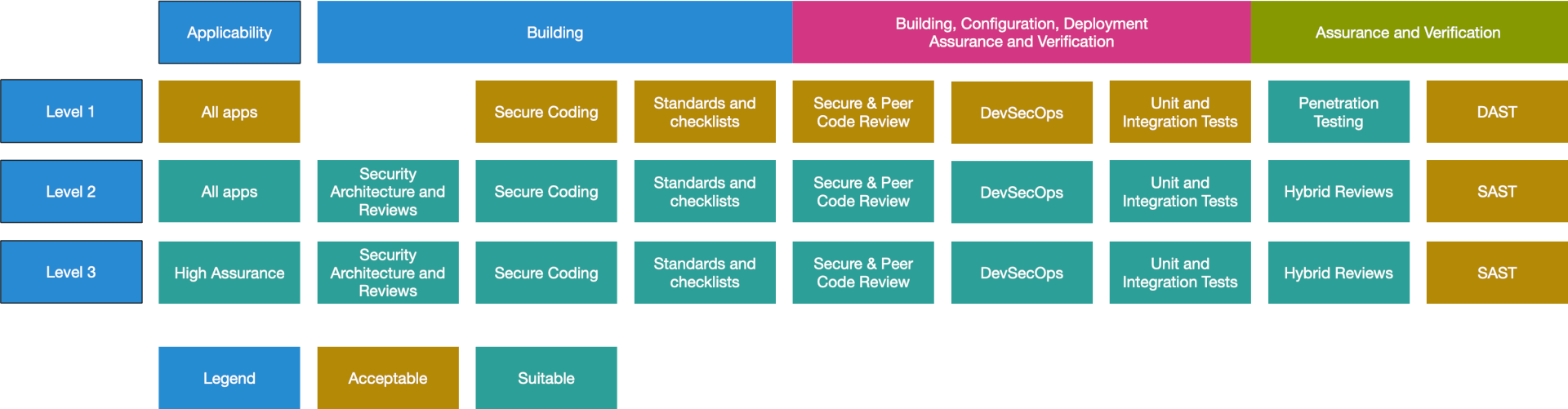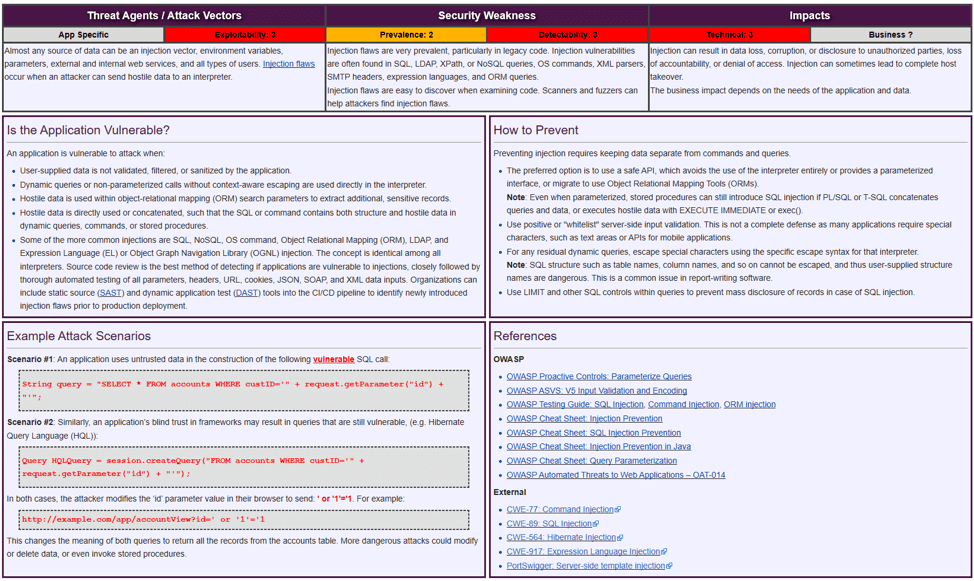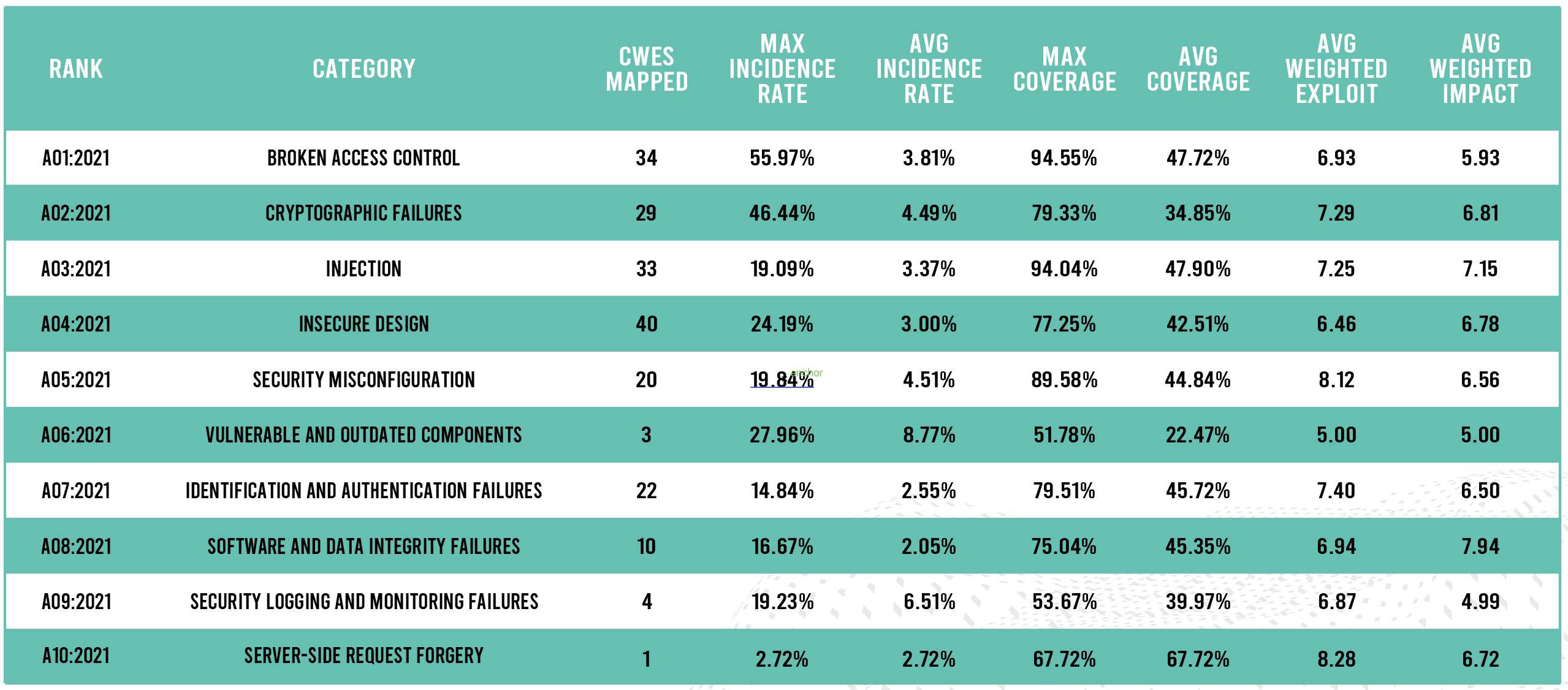
THE 2021 OWASP TOP TEN EMPHASIZES SECURITY CONTROL AREAS OVER INDIVIDUAL VULNERABILITIES FOR IMPROVED RISK MANAGEMENT
OWASP Top 10 Proactive Controls IEEE Top 10 Software Security Design Flaws OWASP Top 10 Vulnerabilities Mitigated OWASP Mobile T

OWASP Top 10 Proactive Controls and Exploits - Part 1 - Foundational Topics in Secure Programming | Coursera
top-10-proactive-controls/introduction.rst at master · owasp-russia/top-10- proactive-controls · GitHub